The Beginners Guide to Private Investigation
April 05, 2018
[Massive Guide] So you want to RAT? Let me help you mate! [Part - 2]
Setting up a DNS
Why do you need a DNS? Fact is that you don't NEED a DNS. But if you don't have one and your IP changes all of your clients will be gone. You don't want that now do you?
Yeah that's what I thought. Now there's 2 free DNS providers and 1 paid provider that are now accepted on HF.
FagDNS found at fagdns.su (FREE)
freenom found at freenom.com (FREE)
Yeah that's what I thought. Now there's 2 free DNS providers and 1 paid provider that are now accepted on HF.
FagDNS found at fagdns.su (FREE)
freenom found at freenom.com (FREE)
I can't help you set up Armada's DNS but the instructions he gives you are more than clear. Well, let's get onto setting up the free DNS alternatives.
Freenom - Free DNS
(Full credit to Neos for the pictures)
- If you plan on using a VPN connect to it right now. If not skip this step.
- Head over to freenom.com and check for an available domain.
- Head over to freenom.com and check for an available domain.
- Take one of the free ones and click on 'get it now!'
- At the right select the period you want to get it for. (You can choose upto 1 year for free!)
- As with any website you will be asked to register an email and all the other stuff. You can use random information but make sure you have access to the email!
- At the right select the period you want to get it for. (You can choose upto 1 year for free!)
- As with any website you will be asked to register an email and all the other stuff. You can use random information but make sure you have access to the email!
- Now that you have your domain head over to this link. https://my.freenom.com/clientarea.php?action=domains (You can navigate there by clicking on domains --> my domains)
- There you will want to click on manage domain followed by manage freenom DNS.
- Here you will be greeted by the following.
- There you will want to click on manage domain followed by manage freenom DNS.
- Here you will be greeted by the following.
- You can leave everything here as the default setting. The only thing you need to change is the target.
- The target will be the IP shown at canyouseeme.org
- Fill in that IP as the target and hit save changes. Your DNS will now be active after 10 - 20 minutes!
- You've succefully created a DNS! After waiting 20 minutes you can go onto testing.
- The target will be the IP shown at canyouseeme.org
- Fill in that IP as the target and hit save changes. Your DNS will now be active after 10 - 20 minutes!
- You've succefully created a DNS! After waiting 20 minutes you can go onto testing.
Testing your DNS
You've created your DNS! Congrats man. Now let's see if it's actually working properly.
- Open your command prompt and type in the following command.
- ping 'yourdnshere' without the ''
- If you see the following but with your IP there then your DNS is working properly!
- Open your command prompt and type in the following command.
- ping 'yourdnshere' without the ''
- If you see the following but with your IP there then your DNS is working properly!
Setting up a RAT
So you've port forwarded and set up a DNS and are ready to embark on the RAT adventure?
PAID
Luminositylink
Orcus
RevCode Webmonitor
Imminent Monitor 4.3 (C# port)
Remcos v1.6.2 Professional
FREE
njRAT
Babylon
Quasar
Darktrack
Luminositylink
Every RAT is basically pre-configured. All that's left to do is build your binary. (The thing you give to your clients)
Due to the max. amount of images some of these will be links instead. My apologies for this.
Luminosity's startup. (Client builder tab)
Due to the max. amount of images some of these will be links instead. My apologies for this.
Luminosity's startup. (Client builder tab)
Crypter startup.
Orcus
- Connect to a VPN if you are using one if not skip this step.
- Start by opening the Orcus server you made in the 'testing your port' section.
- Open Orcus main administration.
- IP = Your external IP found at canyouseeme.org
- Port = Your open port which you configured in the orcus server.
- Password = Your password which you configured in the orcus server.
- Hit connect and you are nog logged into your Orcus. You can now go into building a binary.
Every RAT is basically pre-configured. All that's left to do is build your binary.
Due to the max. amount of images some of these will be links instead. My apologies for this.
General settings - Enable what you feel like.
Connection
- Start by opening the Orcus server you made in the 'testing your port' section.
- Open Orcus main administration.
- IP = Your external IP found at canyouseeme.org
- Port = Your open port which you configured in the orcus server.
- Password = Your password which you configured in the orcus server.
- Hit connect and you are nog logged into your Orcus. You can now go into building a binary.
Every RAT is basically pre-configured. All that's left to do is build your binary.
Due to the max. amount of images some of these will be links instead. My apologies for this.
General settings - Enable what you feel like.
Connection
Protection - Enable what you feel like.
Installation
Installation
Assembly information - Fill in if you want.
Plugins - Use what you want to use.
Build - Enable orcus patcher if you're not testing! Leave it disabled if you're testing.
Crypter startup
Disable EVERYTHING that you can disable and enable it in the crypter.
(Make sure you still have your DNS and port enabled in the connection tab!)
Plugins - Use what you want to use.
Build - Enable orcus patcher if you're not testing! Leave it disabled if you're testing.
Crypter startup
Disable EVERYTHING that you can disable and enable it in the crypter.
(Make sure you still have your DNS and port enabled in the connection tab!)
RevCode Webmonitor
Log in on their website https://yourusernamehere.revcode.eu/index.php and click on 'Client'.
Install = Will make sure the client comes back upon restarting their computer. Enable if you want.
Persistence = Will prevent closure of the client process. Enable if you want.
Click on 'Generate & Download' and EXTRACT your client file (.exe) to your desktop.
Your file is now ready to be sent to your clients.
Persistence = Will prevent closure of the client process. Enable if you want.
Click on 'Generate & Download' and EXTRACT your client file (.exe) to your desktop.
Your file is now ready to be sent to your clients.
Imminent Monitor 4.3 (C# port)
THINGS TO NOTE:
- Everything in module protection is your own choise.
- I personally recommend only using hide file + registry persistence.
- Everything in assembly information is optional and not necessary.
- In compile settings make sure hidden mode is ENABLED.
- Everything in module protection is your own choise.
- I personally recommend only using hide file + registry persistence.
- Everything in assembly information is optional and not necessary.
- In compile settings make sure hidden mode is ENABLED.
Imminent's startup
Crypter's startup
Disable EVERYTHING in module protection and assembly information.
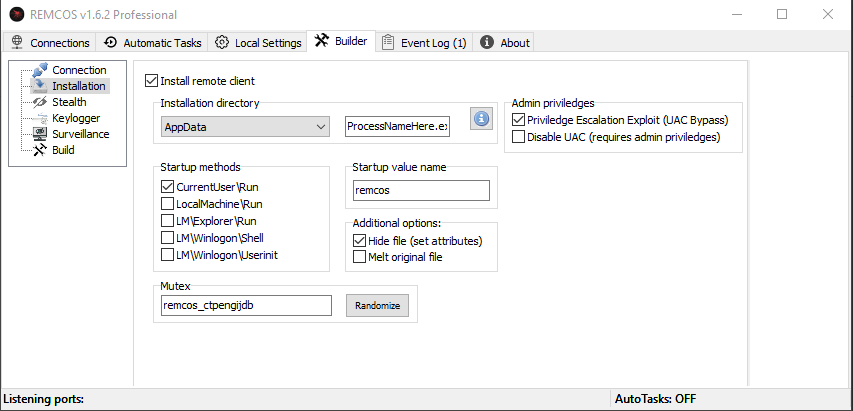
Remcos v1.6.2 Professional
Remcos startup.
Connection tab: Fill in your DNS/IP, port and hit add.
Installation tab:
Connection tab: Fill in your DNS/IP, port and hit add.
Installation tab:
Stealth tab: Enable stealth, NO INJECTION, enable the anti's you want. (VMware, Virtualbox)
Keylogger tab: Enable whatever keylogger you want. (I personally recommend log everything)
Surveillance tab: Enable whatever you want. (I recommend leaving empty)
Build tab: Choose 'Do Not Compress' and click build.
njRATKeylogger tab: Enable whatever keylogger you want. (I personally recommend log everything)
Surveillance tab: Enable whatever you want. (I recommend leaving empty)
Build tab: Choose 'Do Not Compress' and click build.
Every RAT is basically pre-configured. All that's left to do is build your binary.
Due to the max. amount of images some of these will be links instead. My apologies for this.
Due to the max. amount of images some of these will be links instead. My apologies for this.
njRAT's startup.
Babylon
(What does Personal mean? It's whatever you filled in when adding the port, varies for everyone)
Babylon startup. (Just click build when you have the settings from the pictures below)
Crypter startup. (LEAVE EVERYTHING ELSE DEFAULT SETTINGS)
Quasar
Quasar's startup.
- Open your builder. Go to the 'connection settings' tab.
- Fill in your DNS in IP/hostname and your open port in Port.
- Click 'add host' and you should see this.
- Open your builder. Go to the 'connection settings' tab.
- Fill in your DNS in IP/hostname and your open port in Port.
- Click 'add host' and you should see this.
- In the 'installation' tab tick 'install client' and 'run client when the computer starts'. (Feel free to use whatever settings you like just make sure you have those 2 enabled)
- Assembly and surveillance settings are your personal choise.
- When you've gone through all tabs click 'build'.
- Assembly and surveillance settings are your personal choise.
- When you've gone through all tabs click 'build'.
Crypters startup.
- Open your builder. Go to the 'connection settings' tab.
- Fill in your DNS in IP/hostname and your open port in Port.
- Click 'add host' and you should see this.
- Open your builder. Go to the 'connection settings' tab.
- Fill in your DNS in IP/hostname and your open port in Port.
- Click 'add host' and you should see this.
- In 'installation settings' make sure EVERYTHING is disabled.
- Enable the keylogger from the 'surveillance' tab if you want.
- Click build.
Darktrack's startup.
- Click on 'create server' right click on profiles and add a profile.
- Double click that profile then click on 'connection settings'.
- Click 'add IP adress' and fill in your DNS.
- At the right you have 3 boxes. Top = Your open port. Middle = Your password (configured in client settings) Bot= Client ID
- Fill in those boxes and you should have this.
- Click on 'create server' right click on profiles and add a profile.
- Double click that profile then click on 'connection settings'.
- Click 'add IP adress' and fill in your DNS.
- At the right you have 3 boxes. Top = Your open port. Middle = Your password (configured in client settings) Bot= Client ID
- Fill in those boxes and you should have this.
- Go to the 'installation' tab and tick both 'installation' and 'startup'. (change whatever you want just make sure you have those 2 settings enabled!)
- Go to the 'additional' tab and tick persistant server if you so choose.
- Go to the 'security' tab and tick what you want. (I recommend only using Anti VM-ware/PC/Virtualbox)
- Go to the 'build' tab and DON'T use the UPX option. Just click build and you are done.
- Go to the 'additional' tab and tick persistant server if you so choose.
- Go to the 'security' tab and tick what you want. (I recommend only using Anti VM-ware/PC/Virtualbox)
- Go to the 'build' tab and DON'T use the UPX option. Just click build and you are done.
Crypter's startup.
- Click on 'create server' right click on profiles and add a profile.
- Double click that profile then click on 'connection settings'.
- Click 'add IP adress' and fill in your DNS.
- At the right you have 3 boxes. Top = Your open port. Middle = Your password (configured in client settings) Bot= Client ID
- Fill in those boxes and you should have this.
- Click on 'create server' right click on profiles and add a profile.
- Double click that profile then click on 'connection settings'.
- Click 'add IP adress' and fill in your DNS.
- At the right you have 3 boxes. Top = Your open port. Middle = Your password (configured in client settings) Bot= Client ID
- Fill in those boxes and you should have this.
- Disable EVERYTHING in every other tab and build your file in the 'build' tab. (DON'T TICK THE UPX OPTION)
How to test your stub properly
What do you mean? Test it properly?
Well, using the wrong IP inside of your builder usually leads to no connection. As most of you might think there's multiple IP's to use in multiple situations. You can find them down below.
BUILD YOUR STUB ACCORDING THE 'SETTING UP YOUR RAT' SECTION!
Alot of you are testing your stubs the wrong way, making you think things are broken while that might actually not be the case. Here's how you test your stub properly. (All of this assumes you are running your RAT on your actual pc and not somewhere else)
Where am I testing my stub?
1) On the same computer you're running your RAT on.
2) On a VM on the same computer that you're running your RAT.
3) A different computer in the same network.
4) An outside computer outside of your network.
What IP do I need for that?
1) SAME COMPUTER = localhost or 127.0.0.1
2) VM SAME COMPUTER = Your IPv4 or when using a VPN your public IP (found at canyouseeme.org)
3) Different computer same network = Your IPv4 or when using a VPN your public IP (found at canyouseeme.org)
4) Computer outside of your network = Your public IP found at canyouseeme.org or your DNS.
Couple of examples.
1) Testing on my own computer --> https://gyazo.com/26352d88a01457884aa949c5a32949e6
2) Testing on my own VM (no VPN) --> https://gyazo.com/6b9590b953c96285083efb9894c1aea2
3) Testing outside of network --> https://gyazo.com/2f3586ac057ed84882e55c3e2681d07c
HELP NO CONNECTION!!
Calm down, don't panic. This guide WILL have the fix you're looking for but start by checking the following:
- Is my stub crypted? Always test connections uncrypted! This way you'll know if it was your crypter that broke the stub or not.
- Did my AV remove it? It might not look like it, but this is the case 95% of the time. Go check if the process is actually running.
- Am I being a dumbo? Did you misread a portion of my guide? It's very possible, go read over it again.
Well, using the wrong IP inside of your builder usually leads to no connection. As most of you might think there's multiple IP's to use in multiple situations. You can find them down below.
BUILD YOUR STUB ACCORDING THE 'SETTING UP YOUR RAT' SECTION!
Alot of you are testing your stubs the wrong way, making you think things are broken while that might actually not be the case. Here's how you test your stub properly. (All of this assumes you are running your RAT on your actual pc and not somewhere else)
Where am I testing my stub?
1) On the same computer you're running your RAT on.
2) On a VM on the same computer that you're running your RAT.
3) A different computer in the same network.
4) An outside computer outside of your network.
What IP do I need for that?
1) SAME COMPUTER = localhost or 127.0.0.1
2) VM SAME COMPUTER = Your IPv4 or when using a VPN your public IP (found at canyouseeme.org)
3) Different computer same network = Your IPv4 or when using a VPN your public IP (found at canyouseeme.org)
4) Computer outside of your network = Your public IP found at canyouseeme.org or your DNS.
Couple of examples.
1) Testing on my own computer --> https://gyazo.com/26352d88a01457884aa949c5a32949e6
2) Testing on my own VM (no VPN) --> https://gyazo.com/6b9590b953c96285083efb9894c1aea2
3) Testing outside of network --> https://gyazo.com/2f3586ac057ed84882e55c3e2681d07c
HELP NO CONNECTION!!
Calm down, don't panic. This guide WILL have the fix you're looking for but start by checking the following:
- Is my stub crypted? Always test connections uncrypted! This way you'll know if it was your crypter that broke the stub or not.
- Did my AV remove it? It might not look like it, but this is the case 95% of the time. Go check if the process is actually running.
- Am I being a dumbo? Did you misread a portion of my guide? It's very possible, go read over it again.
Common RAT settings explained (open for suggestions)
- Installation/Startup: Required for your client to come back after he restarts his computer.
- Persistance/Respawn/Critical Process/: Will protect your process from being killed in the task manager.
- Mutex: It's a key preventing other RATs with the same key to run on that system. (To make sure you never run your RAT twice on accident)
- Anti Virtual Machine/VM: Prevent your RAT from being run on a virtual machine.
- Silent/Hidden mode: Required to prevent your client from noticing that your RAT is running.
- Melt: Your file will be removed when executed. (The original, not your startup process)
- Request elevation: Will request administrator permissions from your client.
- BSoD: Will generate a blue screen of death upon trying to kill your process.
- Persistance/Respawn/Critical Process/: Will protect your process from being killed in the task manager.
- Mutex: It's a key preventing other RATs with the same key to run on that system. (To make sure you never run your RAT twice on accident)
- Anti Virtual Machine/VM: Prevent your RAT from being run on a virtual machine.
- Silent/Hidden mode: Required to prevent your client from noticing that your RAT is running.
- Melt: Your file will be removed when executed. (The original, not your startup process)
- Request elevation: Will request administrator permissions from your client.
- BSoD: Will generate a blue screen of death upon trying to kill your process.
Common crypter settings explained (open for suggestions)
- Inject into: Will inject your 'RAT' inside of an already existing process.
- Startup/Installation: Required for your client to come back after he restarts his computer.
- Binder: Bind an already existing file to your RAT which will open at the same time. (ex: Pictures)
- Icons: Used to change the icon from your .exe (basically a MUST)
- Assembly: Used to change the assembly from your .exe (basically a MUST)
- Melt: Your file will be removed when executed. (The original, not your startup process)
- Fake error: Will generate a fake error of your choosing to show once your file is ran.
- Extension spoofer: Allows you to spoof the extension of your .exe (not recommended to do this)
- Startup/Installation: Required for your client to come back after he restarts his computer.
- Binder: Bind an already existing file to your RAT which will open at the same time. (ex: Pictures)
- Icons: Used to change the icon from your .exe (basically a MUST)
- Assembly: Used to change the assembly from your .exe (basically a MUST)
- Melt: Your file will be removed when executed. (The original, not your startup process)
- Fake error: Will generate a fake error of your choosing to show once your file is ran.
- Extension spoofer: Allows you to spoof the extension of your .exe (not recommended to do this)
Crypting your RAT
Cyberseal
Data Protector V4
Cyberseal
Dear Friend, crypting. Nightmare of many, including myself.
Sadly there's no easy way to go about it, keep trying and you'll get it FUD sometime!
- First of all you will need to figure out if you're using your crypters startup or not.
- It's usually always recommended to do this, but remains your own choise. (in most cases)
- Let's say you're crypting a .NET based RAT. (Ex. Luminosity, Orcus, Nanocore) you are confined to using the 'inject into self' option if you plan on using your RAT's startup. (Your file is likely to corrupt if you don't do this)
- If you plan on using your crypters startup or are crypting a native RAT you can use other injection methods although I myself don't personally recommend it.
- Now that you've read all of that let's get onto crypting.
Sadly there's no easy way to go about it, keep trying and you'll get it FUD sometime!
- First of all you will need to figure out if you're using your crypters startup or not.
- It's usually always recommended to do this, but remains your own choise. (in most cases)
- Let's say you're crypting a .NET based RAT. (Ex. Luminosity, Orcus, Nanocore) you are confined to using the 'inject into self' option if you plan on using your RAT's startup. (Your file is likely to corrupt if you don't do this)
- If you plan on using your crypters startup or are crypting a native RAT you can use other injection methods although I myself don't personally recommend it.
- Now that you've read all of that let's get onto crypting.
RAT startup.
(I'm crypting Luminosity here for anyone wondering)
- Open up Cyberseal and choose the file to be crypted.
- Tick 'itself' and injection method I personally like to use polymorphic stairs.
- Head over to the 'options' tab.
- Here you will want to choose an icon for your file.
- When you've created the icon as described in the guide click 'browse' and add the icon to your file.
- Now go over to the 'assembly' tab.
- At the bottom you will see 'clone assembly' click that and clone the assembly from an existing legitimate program. (Honestly this is the part which makes crypting hard)
- You're done. Click seal and go scan your file on scan.majyx.net
- Is your file not FUD? Try different assemblies, the problem does NOT lie with your icon.
- Tried bunch of different assemblies but can't find one that works?
- Instead of changing assemblies keep the same assembly and bump your file by 20 - 60kb. (done in the options tab)
- Crypt, not FUD? Bump by 60 - 100kb, crypt. Not FUD? Bump by 100 - 160kb and repeat until it's FUD.
- Here you will want to choose an icon for your file.
- When you've created the icon as described in the guide click 'browse' and add the icon to your file.
- Now go over to the 'assembly' tab.
- At the bottom you will see 'clone assembly' click that and clone the assembly from an existing legitimate program. (Honestly this is the part which makes crypting hard)
- You're done. Click seal and go scan your file on scan.majyx.net
- Is your file not FUD? Try different assemblies, the problem does NOT lie with your icon.
- Tried bunch of different assemblies but can't find one that works?
- Instead of changing assemblies keep the same assembly and bump your file by 20 - 60kb. (done in the options tab)
- Crypt, not FUD? Bump by 60 - 100kb, crypt. Not FUD? Bump by 100 - 160kb and repeat until it's FUD.
Crypter startup.
(I'm crypting Luminosity here for anyone wondering)
- Open up Cyberseal and choose the file to be crypted.
- Tick 'itself' and injection method I personally like to use polymorphic stairs.
- Head over to the 'options' tab.
- Here you will enable startup. Enable it and choose the folder for your file to be dropped in. (I personally prefer appdata)
- Here you will enable startup. Enable it and choose the folder for your file to be dropped in. (I personally prefer appdata)
- You will also want to choose an icon for your file. CREATE YOUR ICON USING THE FOLLOWING TUTORIAL: https://hackforums.net/showthread.php?tid=5182868
- When you've created the icon as described in the guide click 'browse' and add the icon to your file.
- Now go over to the 'assembly' tab.
- At the bottom you will see 'clone assembly' click that and clone the assembly from an existing legitimate program. (Honestly this is the part which makes crypting hard)
- Now head over to the 'others' tab.
- Here you will enable your persistence. Choose either BSoD or the regular persistence. It's not recommended to use both and I prefer the regular persistence personally.
- It's recommended to have a delayed execution altho not necessary.
- You're done. Click seal and go scan your file on scan.majyx.net
- Is your file not FUD? Try different assemblies, the problem does NOT lie with your icon.
- Tried bunch of different assemblies but can't find one that works?
- Instead of changing assemblies keep the same assembly and bump your file by 20 - 60kb. (done in the options tab)
- Crypt, not FUD? Bump by 60 - 100kb, crypt. Not FUD? Bump by 100 - 160kb and repeat until it's FUD.
- When you've created the icon as described in the guide click 'browse' and add the icon to your file.
- Now go over to the 'assembly' tab.
- At the bottom you will see 'clone assembly' click that and clone the assembly from an existing legitimate program. (Honestly this is the part which makes crypting hard)
- Now head over to the 'others' tab.
- Here you will enable your persistence. Choose either BSoD or the regular persistence. It's not recommended to use both and I prefer the regular persistence personally.
- It's recommended to have a delayed execution altho not necessary.
- You're done. Click seal and go scan your file on scan.majyx.net
- Is your file not FUD? Try different assemblies, the problem does NOT lie with your icon.
- Tried bunch of different assemblies but can't find one that works?
- Instead of changing assemblies keep the same assembly and bump your file by 20 - 60kb. (done in the options tab)
- Crypt, not FUD? Bump by 60 - 100kb, crypt. Not FUD? Bump by 100 - 160kb and repeat until it's FUD.
Static Crypt
- First of all you will need to figure out if you're using your crypters startup or not.
- It's usually always recommended to do this, but remains your own choise. (in most cases)
- Let's say you're crypting a .NET based RAT. (Ex. Luminosity, Orcus, Nanocore) you are confined to using the 'inject into self' option if you plan on using your RAT's startup. (Your file is likely to corrupt if you don't do this)
- If you plan on using your crypters startup or are crypting a native RAT you can use other injection methods although I myself don't personally recommend it.
- Now that you've read all of that let's get onto crypting.
- It's usually always recommended to do this, but remains your own choise. (in most cases)
- Let's say you're crypting a .NET based RAT. (Ex. Luminosity, Orcus, Nanocore) you are confined to using the 'inject into self' option if you plan on using your RAT's startup. (Your file is likely to corrupt if you don't do this)
- If you plan on using your crypters startup or are crypting a native RAT you can use other injection methods although I myself don't personally recommend it.
- Now that you've read all of that let's get onto crypting.
RAT startup.
- Start by opening static crypt.
- Open the 'main' tab and choose the file you wish to encrypt.
- Click on the 'crypt' tab you'll see that your injection method will be chosen for you.
- Head over to the 'extra' tab
- At the right you will see '.exe' click that and clone the assembly from an existing legitimate program. (Honestly this is the part which makes crypting hard)
- Once you've done that go back to the 'crypt' tab and press crypt.
- You've now got a file without an icon which is likely to cause a lot of detections.
- You will want to make an icon following this tutorial. https://hackforums.net/showthread.php?tid=5182868
- Once you've got the icon open up the icon changer.
- Click on .Exe and choose the file you just crypted.
- It will give you multiple of those icons below that.
- Start by opening static crypt.
- Open the 'main' tab and choose the file you wish to encrypt.
- Click on the 'crypt' tab you'll see that your injection method will be chosen for you.
- Head over to the 'extra' tab
- At the right you will see '.exe' click that and clone the assembly from an existing legitimate program. (Honestly this is the part which makes crypting hard)
- Once you've done that go back to the 'crypt' tab and press crypt.
- You've now got a file without an icon which is likely to cause a lot of detections.
- You will want to make an icon following this tutorial. https://hackforums.net/showthread.php?tid=5182868
- Once you've got the icon open up the icon changer.
- Click on .Exe and choose the file you just crypted.
- It will give you multiple of those icons below that.
- Choose the with the HIGHEST width and click on that.
- Now click on 'replace icon' and choose the icon you made with the tutorial earlier.
- Althought it looks like the icon didn't change, it DID. Don't worry.
- You can verify by dragging your .exe into a different folder and the icon will change.
- Your file is ready to be scanned on scan.majyx.net
- Is your file not FUD? Try different assemblies, the problem does NOT lie with your icon.
- Tried bunch of different assemblies but can't find one that works?
- Instead of changing assemblies keep the same assembly and bump your file by 20 - 60kb. (done in the options tab)
- Crypt, not FUD? Bump by 60 - 100kb, crypt. Not FUD? Bump by 100 - 160kb and repeat until it's FUD.
- Now click on 'replace icon' and choose the icon you made with the tutorial earlier.
- Althought it looks like the icon didn't change, it DID. Don't worry.
- You can verify by dragging your .exe into a different folder and the icon will change.
- Your file is ready to be scanned on scan.majyx.net
- Is your file not FUD? Try different assemblies, the problem does NOT lie with your icon.
- Tried bunch of different assemblies but can't find one that works?
- Instead of changing assemblies keep the same assembly and bump your file by 20 - 60kb. (done in the options tab)
- Crypt, not FUD? Bump by 60 - 100kb, crypt. Not FUD? Bump by 100 - 160kb and repeat until it's FUD.
Crypter startup.
- Open the 'main' tab and choose the file you wish to encrypt.
- You will also want to enable 'startup' and the folder it gets dropped in. (Usually I go for %appdata%)
- You will also want to enable persistence here under 'settings.'
- Open the 'main' tab and choose the file you wish to encrypt.
- You will also want to enable 'startup' and the folder it gets dropped in. (Usually I go for %appdata%)
- You will also want to enable persistence here under 'settings.'
- Click on the 'crypt' tab you'll see that your injection method will be chosen for you.
- Head over to the 'extra' tab
- At the right you will see '.exe' click that and clone the assembly from an existing legitimate program. (Honestly this is the part which makes crypting hard)
- Once you've done that go back to the 'crypt' tab and press crypt.
- You've now got a file without an icon which is likely to cause a lot of detections.
- You will want to make an icon following this tutorial. https://hackforums.net/showthread.php?tid=5182868
- Once you've got the icon open up the icon changer.
- Click on .Exe and choose the file you just crypted.
- It will give you multiple of those icons below that.
- Head over to the 'extra' tab
- At the right you will see '.exe' click that and clone the assembly from an existing legitimate program. (Honestly this is the part which makes crypting hard)
- Once you've done that go back to the 'crypt' tab and press crypt.
- You've now got a file without an icon which is likely to cause a lot of detections.
- You will want to make an icon following this tutorial. https://hackforums.net/showthread.php?tid=5182868
- Once you've got the icon open up the icon changer.
- Click on .Exe and choose the file you just crypted.
- It will give you multiple of those icons below that.
- Choose the with the HIGHEST width and click on that.
- Now click on 'replace icon' and choose the icon you made with the tutorial earlier.
- Althought it looks like the icon didn't change, it DID. Don't worry.
- You can verify by dragging your .exe into a different folder and the icon will change.
- Your file is ready to be scanned on scan.majyx.net
- Is your file not FUD? Try different assemblies, the problem does NOT lie with your icon.
- Tried bunch of different assemblies but can't find one that works?
- Instead of changing assemblies keep the same assembly and bump your file by 20 - 60kb. (done in the options tab)
- Crypt, not FUD? Bump by 60 - 100kb, crypt. Not FUD? Bump by 100 - 160kb and repeat until it's FUD.
- Now click on 'replace icon' and choose the icon you made with the tutorial earlier.
- Althought it looks like the icon didn't change, it DID. Don't worry.
- You can verify by dragging your .exe into a different folder and the icon will change.
- Your file is ready to be scanned on scan.majyx.net
- Is your file not FUD? Try different assemblies, the problem does NOT lie with your icon.
- Tried bunch of different assemblies but can't find one that works?
- Instead of changing assemblies keep the same assembly and bump your file by 20 - 60kb. (done in the options tab)
- Crypt, not FUD? Bump by 60 - 100kb, crypt. Not FUD? Bump by 100 - 160kb and repeat until it's FUD.
Common questions (F.A.Q)
Q: What's the best RAT?
A: There is no best RAT. Every RAT has it's own strong and weak points.
Q: What's the best crypter?
A: Currently I believe Cyberseal is the best crypter around. (on 04/07/2016)
Q: Do you need a VPN?
A: No, you do not. Just like you don't need a seatbelt when driving but we all know what happens if something goes wrong and you aren't wearing one.
Q: Do you need a DNS?
A: No you don't but you'll permanently lose all your clients if your IP changes.
Q: Personal recommendations?
A: Luminositylink/Orcus with Cyberseal and crypticVPN.
Q: Where can I download Darkcomet?
A: NOWHERE! Darkcomet doesn't exit. Think of it that way.
Q: Should I buy a crypter?
A: Yes, don't even BOTHER with free crypters. Just no.
A: There is no best RAT. Every RAT has it's own strong and weak points.
Q: What's the best crypter?
A: Currently I believe Cyberseal is the best crypter around. (on 04/07/2016)
Q: Do you need a VPN?
A: No, you do not. Just like you don't need a seatbelt when driving but we all know what happens if something goes wrong and you aren't wearing one.
Q: Do you need a DNS?
A: No you don't but you'll permanently lose all your clients if your IP changes.
Q: Personal recommendations?
A: Luminositylink/Orcus with Cyberseal and crypticVPN.
Q: Where can I download Darkcomet?
A: NOWHERE! Darkcomet doesn't exit. Think of it that way.
Q: Should I buy a crypter?
A: Yes, don't even BOTHER with free crypters. Just no.
Don't do ANY of this.
RAT Related
- Do not use Darkcomet for the reason that it has serious security flaws. (I will deny you help if you insist on using this RAT)
- Do not use Blackshades for the reason the police took over the product.
- Do not use NO-IP for the reason that it is monitored by Microsoft.
- Do not use duckDNS for the reason that they'll give you honeypots.
- Never use the same port for 2 RATs. (or program in general)
- Participate in banking fraud.
Crypter Related
- Use startup in both crypter and RAT.
- Use any settings in both crypter and RAT.
- Never crypt a crypted file.
- Inject into a process when using startup on a .NET RAT. (Ex. Luminosity)
- Do not cry to crypter owners about a 10/35 detection rate, it's your own fault.
- Assume scantime and runtime is the same.
- Do not use the website http://www.virustotal.com
- Do not use Darkcomet for the reason that it has serious security flaws. (I will deny you help if you insist on using this RAT)
- Do not use Blackshades for the reason the police took over the product.
- Do not use NO-IP for the reason that it is monitored by Microsoft.
- Do not use duckDNS for the reason that they'll give you honeypots.
- Never use the same port for 2 RATs. (or program in general)
- Participate in banking fraud.
Crypter Related
- Use startup in both crypter and RAT.
- Use any settings in both crypter and RAT.
- Never crypt a crypted file.
- Inject into a process when using startup on a .NET RAT. (Ex. Luminosity)
- Do not cry to crypter owners about a 10/35 detection rate, it's your own fault.
- Assume scantime and runtime is the same.
- Do not use the website http://www.virustotal.com
Statscount
Trending Posts

Cs 1.6 Recoil Controlling
September 24, 2015
The Beginners Guide to Private Investigation
April 05, 2018
Subscribe Us
Total Pageviews
Search
Categories
Contact Form
Created By eaadhar |

![GTA - SA All [PC] Game Missions Save Files, [Bonus Cheats]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEji0bTCRrJKO41LWRud2OPlWVNp3YFMWW6fTKYPF50ctp5sYt5M_qcqbP-ihCtn25AvOb0qr9pH05ktq0577U2U-ZSL8Vn1H3IoEu3pp8-r6zegrO_W1R2SpOiUU4B7HMzx3cBU2Llq7Rc/w680/10h875f.jpg)





















![[Massive Guide] So you want to RAT? Let me help you mate! [Part - 1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi7ErqQB5sOAL6EMSYt6Fz7y4aJJ4n6EaZolvln9HJ5E_WpKj_EgFxfz053bz4E7M7MLN8HBDGqCgmLHZ6kn_PSacj9hndL68JO0tjiu-EuiROQLQespqKIjGOzVeF7smpgKGCtsI8hdWY/w680/anonymous-guide-hacking-isis.png)




0 Comments